In today’s interconnected digital world, the security and integrity of our data have never been more crucial. From personal photos and medical records to financial transactions and corporate secrets, we rely on various mechanisms to keep our information safe from prying eyes and malicious actors.
Two of the most prominent and often misunderstood methods are encryption and hashing. While they might appear similar to the uninitiated, they serve distinct purposes in the vast landscape of cybersecurity. This article aims to demystify these concepts, highlighting their unique roles and differences.
The Basics of Encryption

Encryption is a fascinating process that transforms readable data, known as plaintext, into an unreadable format called ciphertext. This transformation ensures that even if malicious actors intercept the data, they can’t understand it without the right tools.
How Does It Work?
At its core, encryption relies on algorithms and cryptographic keys. The algorithm dictates how the transformation occurs, while the key provides a unique twist to the process. The strength and security of the encryption depend on the combination of the algorithm used and the length and complexity of the key.
For someone to decipher or decrypt the encrypted data, they would need the appropriate key. This dual nature—scrambling and then unscrambling—makes it a powerful tool for protecting data during transmission or while stored. The primary allure of encryption is its reversibility.
With the correct key, one can revert the scrambled data back to its original, readable form. This reversible nature is crucial for scenarios where data needs to be securely transmitted and subsequently accessed in its original form, such as in online banking transactions or secure email communications.
Different Types of Encryption

Broadly, this process falls into two categories: symmetric and asymmetric. Symmetric encryption is like a secure box with a single key; the same key locks (encrypts) and unlocks (decrypts) the box. Both the sender and the receiver must possess this key, making key exchange a challenge.
Asymmetric encryption, conversely, uses a pair of keys: a public key to lock (encrypt) the box and a private key to unlock (decrypt) it. This means anyone can use the public key to encrypt data, but only the holder of the private key can decrypt it, ensuring a higher level of security.
| Aspect | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Type of Encryption | Uses a single key for both encryption and decryption. | Uses a pair of keys: public and private. |
| Key Usage | The same key encrypts and decrypts data. | The public key encrypts the private key decrypts. |
| Key Distribution | Both sender and receiver need the same key. | Public keys are shared, and private keys are kept secret. |
| Security | Key exchange is a challenge, as the key must be kept secure. | More secure due to separate key pairs. |
| Encryption/Decryption | Faster since only one key is used. | Slightly slower due to complex key pairs. |
| Use Cases | File encryption, secure communication. | Digital signatures, secure data sharing. |
Hashing
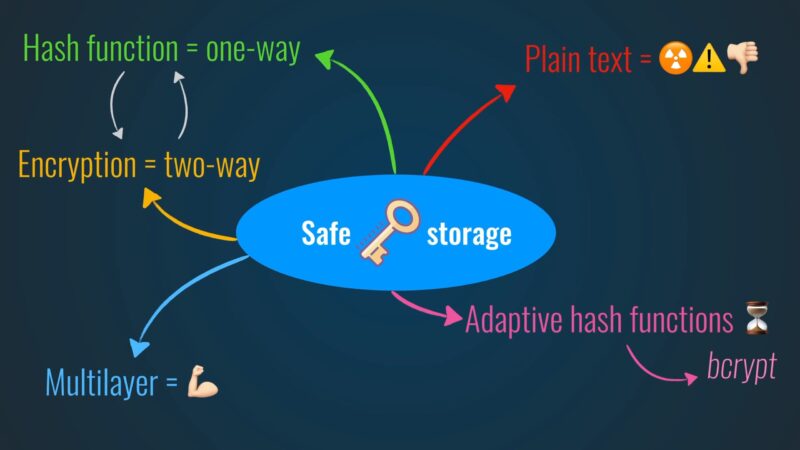
Hashing, unlike encryption, is a one-way street. It takes input data, processes it, and produces a fixed-size string of characters, which often appears random and is unique to the input data.
How Hashing Works?
When data is fed into a hash function, the result is a unique hash value or hash code. Regardless of the size or length of the input, the resulting hash will always be of a consistent length. The magic of hashing is that even a minuscule change in the input—like altering a single character—results in a dramatically different hash value.
Hashing’s primary role is data verification and integrity assurance. Since it’s computationally challenging to find two different inputs that produce the same hash, if the hash value of received data matches the hash value of the original data, it’s a strong indicator that the data remains untampered.
Common Uses
One of the most widespread applications of hashing is in password storage. When you register on a website, instead of storing your actual password, the system stores its hash. Every time you log in, the system hashes the entered password and compares it to the stored hash.
This approach ensures that even if there’s a data breach, attackers get only the hashes, not the actual passwords. Additionally, hashing is used in data verification processes, like ensuring a downloaded file’s integrity by comparing hash values.
Key Differences Between Encryption and Hashing

While both are cornerstones of cybersecurity, encryption, and hashing have distinct characteristics and applications.
Purpose and Functionality
Encryption is primarily about confidentiality. It ensures data remains private by making it unreadable to unauthorized parties. However, the intention is always to decrypt the data later. Hashing, in contrast, is about verification and integrity.
Once data is hashed, it’s not meant to be converted back. Instead, its hash value serves as a reference point for future checks.
Directionality
Encryption is bidirectional. Data is encrypted and then decrypted, moving from a readable to an unreadable state and back again. Hashing is unidirectional. Once data undergoes hashing, there’s no turning back; it’s a one-way journey. This fundamental difference underscores their unique roles in data security.
Practical Applications

Both encryption and hashing are omnipresent, silently working behind the scenes in our daily digital interactions.
Encryption in Everyday Life
Encryption is a silent guardian. When you shop online, the details of your transaction, including your credit card information, are encrypted to shield them from potential eavesdroppers. Secure messaging apps encrypt your conversations, ensuring that only the intended recipient can read your messages.
Even routine activities, like browsing the web, involve encryption, safeguarding your interactions, and ensuring the websites you visit are genuine.
Hashing in Everyday Life
While encryption often takes the limelight, hashing is the unsung hero. Beyond password verification, hashing ensures the integrity of data transfers. For instance, when downloading software, many providers offer hash values for you to verify the downloaded file’s integrity, ensuring it hasn’t been tampered with and is free from malicious alterations. Moreover converting files from one format to another can also play a role. Go here to convert image files from PNG to SVG formats can sometimes enhance the security of visual data, especially when dealing with scalable vector graphics that might be used for secure logos or intricate design elements.
Security Implications

As cyber threats evolve, understanding the strengths and vulnerabilities of both encryption and hashing becomes paramount.
Encryption Vulnerabilities
No security measure is bulletproof, and encryption is no exception. If attackers obtain the encryption key, they can decrypt the data. Furthermore, outdated or weak encryption algorithms can be cracked. It’s vital to stay updated with the latest encryption standards and to safeguard encryption keys meticulously.
Hashing Vulnerabilities
Hashing too has its Achilles’ heel. Weak hash functions can lead to ‘collisions’, where different inputs yield the same hash value, undermining data integrity checks. To bolster hashing’s efficacy, it’s essential to use robust, modern hash functions and employ techniques like ‘salting’ passwords, which adds an extra layer of protection.
FAQs:
What is the “avalanche effect” in hashing?
The avalanche effect means that any change made to an input, no matter how small, will result in a massive change in the output.
Can hashed data be decrypted?
Hashed data cannot be decrypted, making it infeasible to reverse.
Why is hashing preferred for passwords?
Hashing is preferred for passwords because it makes the password shorter and undiscoverable by attackers.
How does the size of the hash output vary with different hashing algorithms?
Different hashing algorithms produce outputs of different sizes. For instance, SHA-256 produces an output of 256 bits, while MD5 gives an output of 128 bits.
What are some common Symmetric Encryption Algorithms?
Advanced Encryption Standard (AES), Blowfish, Twofish, Rivest Cipher (RC4), and Data Encryption Standard (DES).
Conclusion: Choosing the Right Tool for the Job
Both encryption and hashing are invaluable, each shining in its domain. Opt for encryption when the goal is to shield data from unauthorized access but also to retrieve the original data later. This is pivotal for both data in transit (like emails) and data at rest (like stored files).
Hashing is the go-to when the focus is on data verification or storing sensitive data like passwords. Given its one-way nature, hashing is tailor-made for scenarios where reverting to the original data isn’t necessary. In the vast realm of data security, understanding the nuances between encryption and hashing is essential.
By choosing the right tool for the right job, we can ensure our digital world remains both private and trustworthy.






